Blog
Jan 27, 2015
Kali USB – Multiple Persistent Stores
One of the markings of the 1.0.7 Kali release was the introduction of Kali Live USB LUKS encrypted persistent storage, on which we further elaborated in one of our previous blog posts. However, we’re not done yet with USB persistent storage as more features in Kali remain to be explored.
4 min read

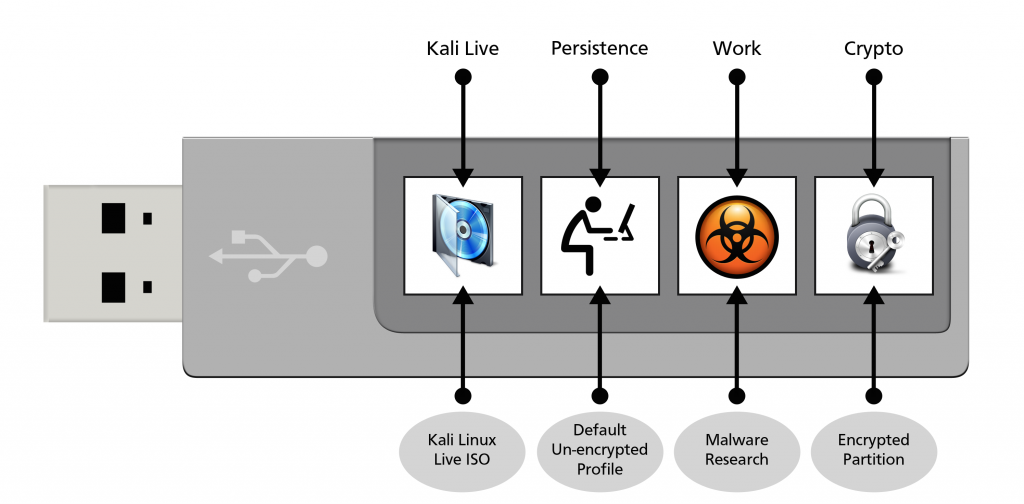
One of the markings of the 1.0.7 Kali release was the introduction of Kali Live USB LUKS encrypted persistent storage, on which we further elaborated in one of our previous blog posts. However, we’re not done yet with USB persistent storage as more features in Kali remain to be explored. The feature we will discuss today boasts the ability to have multiple persistent USB storages which you can choose from at boot time. These multiple persistent storages can be either encrypted, or unencrypted, and can be chosen at boot time using the persistence-label boot parameter.
Multiple Persistent USB Profiles
This persistence feature is extremely useful to us, as we can create profile based persistence storages. For example, we could choose to have a regular persistence partition where all our casual work with Kali is done, as well as a separate persistent partition where we do our malware research. Finally, we also have a third encrypted persistence store, where our confidential documents are kept.
Down to business
Let’s see what it takes to set up a Kali USB switchblade such as this. We’ll start by imaging the Kali ISO onto your USB stick (ours was /dev/sdb). Once done, you can inspect the USB partition structure using parted /dev/sdb print.
[cc lang=”bash”]
dd if=kali-linux-1.0.9a-amd64.iso of=/dev/sdb bs=1M
[/cc]
As we do for normal persistence, we’ll create and format an additional partition on the USB stick. In our example, we create a persistent partition of about 7 GB in size:
[cc lang=”bash”]
root@kali:~# parted
GNU Parted 2.3
Using /dev/sda
Welcome to GNU Parted! Type ‘help’ to view a list of commands.
(parted) print devices
/dev/sda (480GB)
/dev/sdb (31.6GB)
(parted) select /dev/sdb
Using /dev/sdb
(parted) print
Model: SanDisk SanDisk Ultra (scsi)
Disk /dev/sdb: 31.6GB
Sector size (logical/physical): 512B/512B
Partition Table: msdos
Number Start End Size Type File system Flags
1 32.8kB 2988MB 2988MB primary boot, hidden
2 2988MB 3053MB 64.9MB primary fat16
(parted) mkpart primary 3053 10000
(parted) quit
Information: You may need to update /etc/fstab.
[/cc]
We’ll encrypt the partition we created using LUKS, then mount, format and label it:
[cc lang=”bash”]
cryptsetup –verbose –verify-passphrase luksFormat /dev/sdb3
cryptsetup luksOpen /dev/sdb3 my_usb
mkfs.ext3 /dev/mapper/my_usb
e2label /dev/mapper/my_usb persistence[/cc]
We then create our persistence.conf on that partition so changes persist across reboots:
[cc lang=”bash”]
mkdir -p /mnt/my_usb
mount /dev/mapper/my_usb /mnt/my_usb
echo “/ union” > /mnt/my_usb/persistence.conf
umount /dev/mapper/my_usb
cryptsetup luksClose /dev/mapper/my_usb[/cc]
Up to now, we’ve completed the procedure of setting up a regular, encrypted persistence store. Now we can proceed to create a second persistence store – we’ll call it “work” and assign it 5 GB of space.
[cc lang=”bash”]root@kali:~# parted /dev/sdb
GNU Parted 2.3
Using /dev/sdb
Welcome to GNU Parted! Type ‘help’ to view a list of commands.
(parted) print
Model: SanDisk SanDisk Ultra (scsi)
Disk /dev/sdb: 31.6GB
Sector size (logical/physical): 512B/512B
Partition Table: msdos
Number Start End Size Type File system Flags
1 32.8kB 2988MB 2988MB primary boot, hidden
2 2988MB 3053MB 64.9MB primary fat16
3 3053MB 10.0GB 6947MB primary
(parted) mkpart primary 10000 15000
(parted) quit
Information: You may need to update /etc/fstab.
[/cc]
Next, we format the fourth partition and label it “work”.
[cc lang=”bash”]mkfs.ext3 /dev/sdb4
e2label /dev/sdb4 work
[/cc]
[cc lang=”bash”]
mkdir -p /mnt/usb
mount /dev/sdb4 /mnt/usb
echo “/ union” > /mnt/usb/persistence.conf
umount /mnt/usb
[/cc]
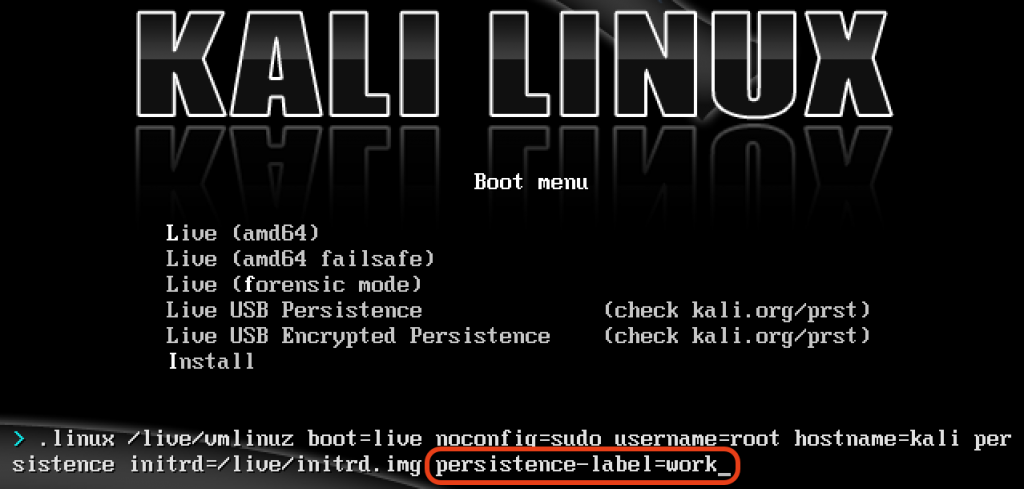
That’s it! Boot the computer, and set it to boot from USB. When the boot menu appears, edit the persistence-label parameter to point to your preferred persistence store as shown below:
Cybersecurity leader resources
Sign up for the Secure Leader and get the latest info on industry trends, resources and best practices for security leaders every other week
Latest from OffSec

Enterprise Security
Red Team vs Blue Team in Cybersecurity
Learn what a red team and blue team in cybersecurity are, pros and cons of both, as well as how they work together.
Dec 13, 2024
13 min read

Enterprise Security
Building a Future-Ready Cybersecurity Workforce: The OffSec Approach to Talent Development
Learn all about our recent webinar “Building a Future-Ready Cyber Workforce: The OffSec Approach to Talent Development”.
Dec 13, 2024
4 min read

Enterprise Security
How to Become the Company Top Cyber Talent Wants to Join
Become the company cybersecurity talent wants to join. Learn how to attract, assess, and retain experts with strategies that set you apart.
Dec 4, 2024
5 min read