Blog
Dec 8, 2014
Bypassing Windows and OSX Logins with NetHunter & Kon-boot
The Kali Linux NetHunter platform has many hidden features which we still haven’t brought to light. One of them is the DriveDroid application and patch set, which have been implemented in NetHunter since v1.0.2. This tool allows us to have NetHunter emulate a bootable ISO or USB, using images of our choosing. That’s right, you can use NetHunter as a boot device which holds a library of bootable ISOs and images…And so we begin:
2 min read

DriveDroid support in Kali Linux NetHunter
The Kali Linux NetHunter platform has many hidden features which we still haven’t brought to light. One of them is the DriveDroid application and patch set, which have been implemented in NetHunter since v1.0.2. This tool allows us to have NetHunter emulate a bootable ISO or USB, using images of our choosing. That’s right, you can use NetHunter as a boot device which holds a library of bootable ISOs and images…And so we begin:
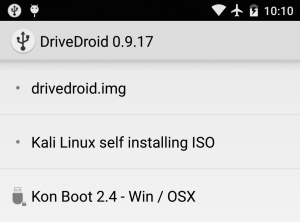
Installing Kali Linux Unattended using your Android Phone
Yes, this is actually doable. We can easily generate a custom Kali ISO which has a self installing preseed file and have NetHunter boot it on a target machine. You load up DriveDroid, select the self installing ISO, plug in the USB cable, and reboot the target computer…..and all of a sudden, the Kali Linux install screen whizzes by, and starts installing itself with no user interaction…
Bypassing Windows and OSX Logins Using NetHunter and Kon-Boot
While the NetHunter HID attacks can provide us pre-programmed keyboard strokes which end up compromising the target machine – what happens if the target machine is turned off, or otherwise requires a login to access? The NetHunter HID attack would be useless at this point. Enter Kon-Boot, a must-have tool for anyone performing physical security assessments. As a quick reminder, Kon-Boot is a boot-kit which will silently boot and bypass the authentication process of Windows/OSX based operating systems, without overwriting your old passwords.
We went ahead and purchased a commercial version of Kon-Boot, and tried using the provided Kon-Boot image file as our bootable USB payload. Lo and behold, when we plugged in our NetHunter device USB cable to a target computer, the Kon-Boot image booted and allowed us to bypass a Windows 8.1 login screen. Check out the video below to see it in action:
Bypass Windows and OSX login with NetHunter and Kon-boot from Offensive Security.
Although this technology isn’t new, this implementation of it is pretty awesome, and complements the NetHunter arsenal of tools and features perfectly. Whats more, this has been battle tested in real-world onsite physical pentests we’ve performed and has proven to be extremely effective.
Stay up to date with Kali Linux NetHunter Features
As NetHunter development continues, we will try our hardest to make sure we keep you updated with all the existing and upcoming features of this awesome platform. To stay updated with our blogs and posts, make sure you follow us on twitter:
Latest from OffSec

Enterprise Security
Red Team vs Blue Team in Cybersecurity
Learn what a red team and blue team in cybersecurity are, pros and cons of both, as well as how they work together.
Dec 13, 2024
13 min read

Enterprise Security
Building a Future-Ready Cybersecurity Workforce: The OffSec Approach to Talent Development
Learn all about our recent webinar “Building a Future-Ready Cyber Workforce: The OffSec Approach to Talent Development”.
Dec 13, 2024
4 min read

Enterprise Security
How to Become the Company Top Cyber Talent Wants to Join
Become the company cybersecurity talent wants to join. Learn how to attract, assess, and retain experts with strategies that set you apart.
Dec 4, 2024
5 min read