Blog
Research & Tutorials

May 12, 2020
9 min read
macOS Kernel Debugging with SIP
As security researchers, we often find ourselves needing to look deep into various kernels to fully understand our target and accomplish our goals. Doing so on the Windows platform is no mystery, as there have been countless well-written posts about kernel debugging setups. For macOS, however, the situation is slightly different. There are many great

Research & Tutorials
Analyzing a Creative Attack Chain Used to Compromise a Web Application
In this piece, we’ll analyze a creative scenario where a malicious actor can use an attack chain to exploit a web application via Simple Network Management Protocol (SNMP) > Cross-site scripting (XSS) > Remote Code Execution (RCE).
Sep 3, 2019
5 min read
Research & Tutorials
Yahoo DOM XSS 0day – Not fixed yet!
After discussing the recent Yahoo DOM XSS 0day with Shahin from Abysssec.com, it was discovered that Yahoo’s fix set in place on 6:20 PM EST, Jan 7th, 2013 is not effective as one would hope.
Jan 8, 2013
2 min read
Research & Tutorials
Onity Door Unlocker, Round Two.
On one of our engagements, we figured an Onity Hotel door unlocker would be useful to us. Inspired by the “James Bond” type setup we saw on the Spiderlabs blog post, we thought we’de try to build a small, simple and “TSA friendly” version of the Onity key unlocker.
Oct 23, 2012
2 min read
Research & Tutorials
Stand-Alone EM4x RFID Harvester
Continuing off from our last RFID Cloning with Proxmark3 post, we wanted to build a small, portable, stand-alone EM4x RFID tag stealer. We needed an easy way of storing multiple tag IDs whilst “rubbing elbows” with company personnel. The proxmark3 seemed liked an overkill and not particularly fast at reading em4x tags so we figured we’d try hooking up our RoboticsConnection RFID reader to a Teensy and see if we could make them play nicely together.
Sep 27, 2012
2 min read
Research & Tutorials
RFID Cloning with Proxmark 3
Our Proxmark 3 (and antennae) finally arrived, and we thought we’d take it for a spin. It’s a great little device for physical pentests, allowing us to capture, replay and clone certain RFID tags.
Sep 24, 2012
5 min read

Research & Tutorials
FreePBX Exploit Phone Home
During a routine scan of new vulnerability reports for the Exploit Database, we came across a single post in full disclosure by Martin Tschirsich, about a Remote Code Execution vulnerability in FreePBX. This vulnerability sounded intriguing, and as usual, required verification in the EDB. At first glance, the vulnerability didn’t jump out at us, especially as we are not familiar with the inner workings of asterisk. After a couple of emails back and forth with Martin, the path to code execution became clearer:
Mar 23, 2012
3 min read

Research & Tutorials
The Art of Human Hacking
It’s hard to believe that the social-engineer.org project began 14 months ago. This project started from a simple idea to build the world’s first framework for social engineers. In these 14 months, this project has grown into the leading resource for all real social engineering education. The CTF that we held at Defcon 18 proved beyond doubt that this resource was greatly required.
Dec 19, 2010
2 min read
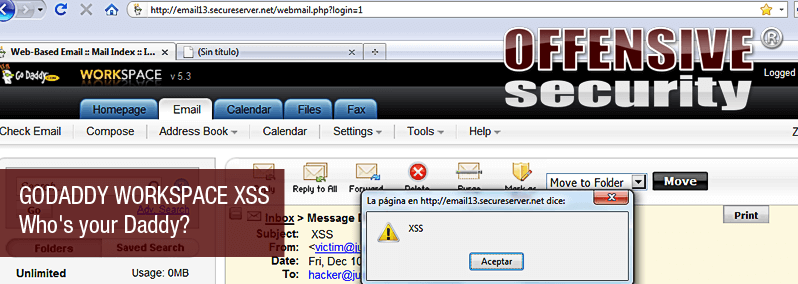
Research & Tutorials
Godaddy Workspace XSS – Who’s your Daddy ?
An interesting submission in from the Exploit Database – a Godaddy workspace XSS vulnerability. Although we did not post it (live site), the vulnerability seems real, and definitely worth mentioning.
Dec 11, 2010
1 min read

Research & Tutorials
Offensive Security Exploit Archive Online
Offensive Security Exploit Database, as well as Vulnerable applications is now Online
Nov 16, 2009
1 min read